New OS, New Malware: Windows 10 Ransomware Scam
Just two weeks after its release, Windows 10 has already been installed for free on more than 70 million PCs. Microsoft is pulling all the stops to make the OS as appealing as possible. It even released a Windows 10 media creation tool to make upgrading to the new OS easier. Unfortunately, all the hype has also reached the attention of cybercriminals.
Windows 10 Ransomware Scam
The new scam campaign was first reported by Cisco just two days after Windows 10 was released. The scam revolves around a spam campaign in which an email containing the CTB-Locker ransomware is circulated.
The Fake email
The legitimate looking email will instruct you to download and install an attached executable file that will allegedly allow you to upgrade your OS to Windows 10 for free.
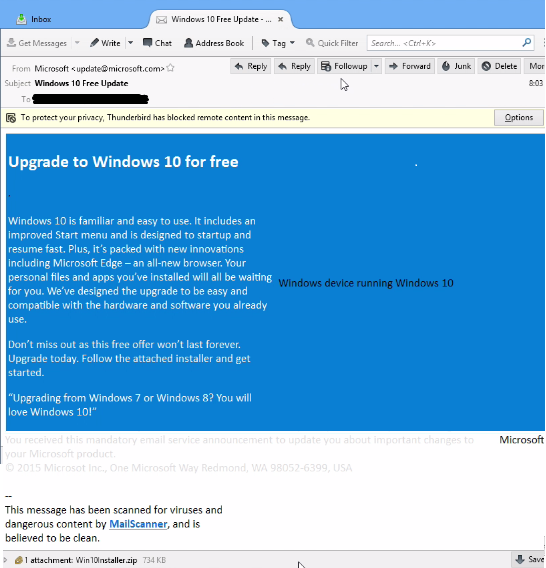
There are several characteristics that make the scam email quite convincing.
- Appearance: The scam email looks just like one that comes from Microsoft, including a similar color scheme.
- Address: The scammers have even managed to spoof the email address update@microsoft.com.
- Disclaimer: There is a dimmed disclaimer text following the email message claiming that the email is a mandatory service announcement.
- Scanned: There is a message before the attachment that states that the email has been scanned was determined to be free of malicious content, and links to an actual open source email filter (mailscanner.info).
The Encryption Notice
The attachment “Win10Installer.zip” contains a ransomware variant called “CTB-Locker,” which is loaded instead of the Windows 10 installer, and which – after the user downloads and extracts the installer files – overtakes all accessible files in a matter of seconds and renders them inaccessible. And, to be sure you are sufficiently alarmed in the process, the CTB-Locker clears the desktop background, seats its own you’ve-been-duped message, and similarly flashes the encryption notice which looks like the below.
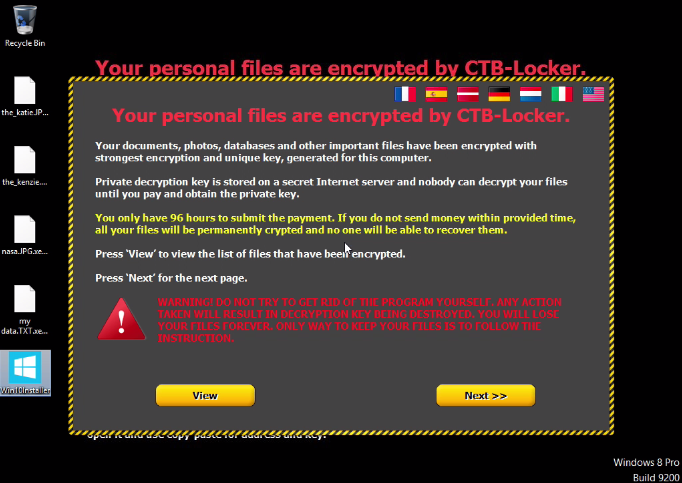
The way the CTB-Locker works is by running through your directories immediately and converts the file name extensions of your files into random ones using an elliptical curve cryptography. This provides the maddening result of you being able to recognize the core file name of your precious files and folders but being completely unable to access them. You instead will be notified that the file you are attempting to access or open is corrupted, damaged, or an unrecognized file type with which you currently have no programs or applications that can open it.
And to ensure anxiety is particularly piqued, CTB-Locker will show you a notice that claims your files will be permanently deleted if payment is not made within 96 hours. An unwelcome timer displays the ticking-down seconds until an impending removal of the secret key to unlock and decrypt the files. In essence, the door on your files will be locked and CTB-Locker will throw away the key. Of course, the notice also provides you with instructions on how to make the payment to make it all go-away. And if negotiating with criminals is against your moral code, plan to say bye- bye to your files, because currently there is no way to retrieve the private key or decrypt your files once CTB-Locker is rooted without paying the ransom.
Constant Vigilance
Given the growing popularity of Windows 10, expect more phishing scams offering free and quick upgrades to follow, especially since Microsoft awards the free upgrade in batches. The best way to avoid falling prey to such schemes is to exercise vigilance and reasonable precaution against all email offers.
Be sure to keep complete and updated backups of all critical data so that if you do fall victim to a virus, you will have a reliable restore point. Image-level backups removes the downside of having to reorganize files after restoring them. And of course be skeptical of what you see on the internet — particularly of offers that seem too good (or too convenient) to be true!
If this has you thinking about backups, security and making sure you are adequately protected against threats like this one, we’re here to help. Use the “Comments & Contact” button below to submit any questions you have about ransomware variants, network security, or to get more information on Dynamic Quest’s services and products.




